Internet Security Router User
’s Manual
Chapter 11. Configuring Remote Access
115
11.5 Configure Firewall for Remote Access
Remote Access is usually used to support mobile users of a company to access their corporate network
without compromising on security. The steps required for configuring the Internet Security Router for remote
access is best explained with an example. The following shows the steps required to configure the Internet
Security Router for the remote users, Richard and Gloria, to access the FTP server located in the protected
network, i.e. corporate LAN. Figure 11.6 shows the network diagram for this example.
1.
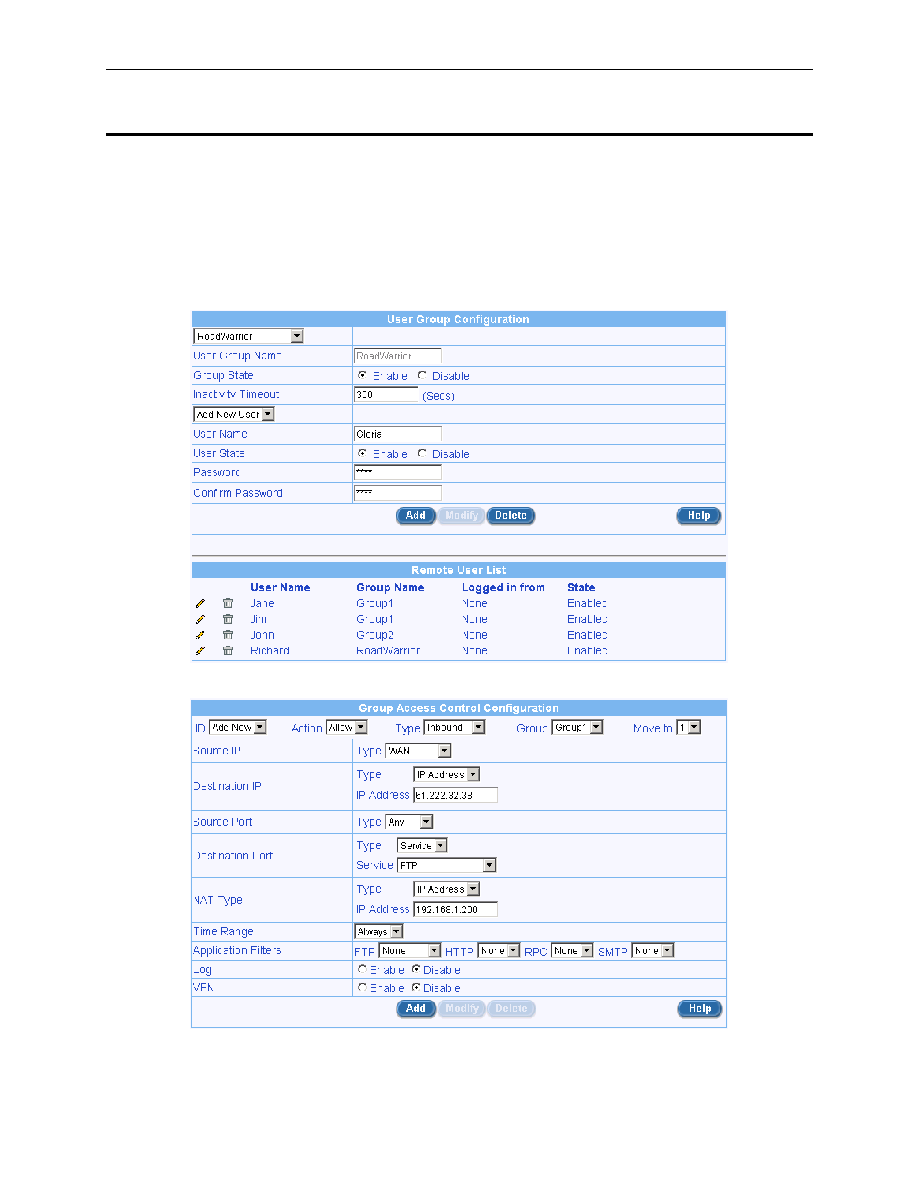
Create remote access users and groups if necessary. Figure 11.7 illustrates the creation of a new
user, Gloria. For details on how to add new users and/or new user group for remote access,
please refer to section 11.2 Manage User Groups and Users.
Figure 11.7. User and User Group Configuration Example
Figure 11.8. Group ACL Configuration Example

