Chapter 10. Configuring VPN
Internet Security Router User
’s Manual
96
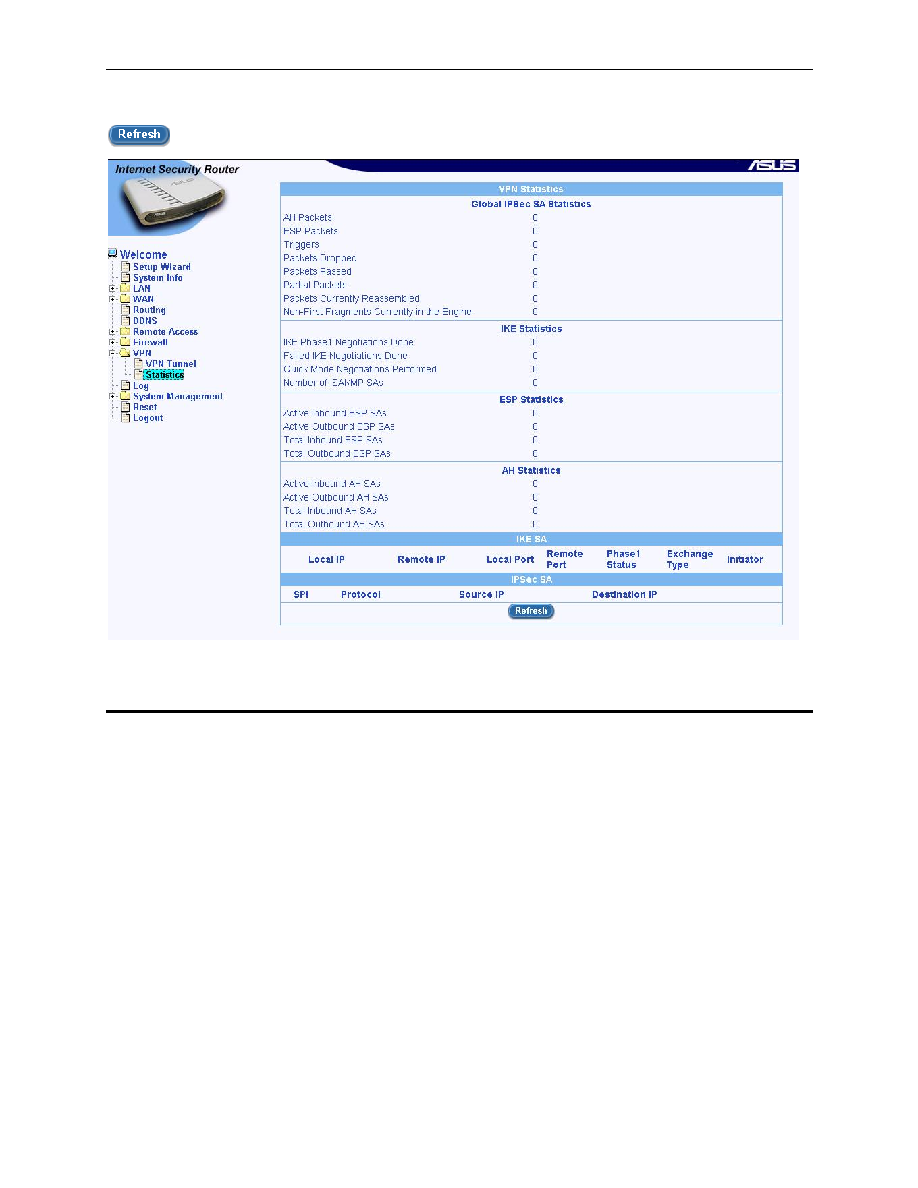
Figure 10.3 shows all the parameters available for VPN connections. To see an updated statistics, click on the
button.
Figure 10.3. VPN Statistics Page
10.6 VPN Connection Examples
Gateways with integrated VPN and Firewall are useful in scenarios where:
„ The traffic between branch offices is protected by VPN and
„ Traffic destined for public Internet goes through Firewall/NAT.
To avoid NAT/IPSec interoperability issues, outgoing traffic is first processed by Firewall/NAT and then by
IPSec. Hence, you must ensure that appropriate Firewall rules are configured to let the VPN traffic goes
through. This section describes these scenarios and presents step-by-step instructions for configuring these
scenarios.
10.6.1 Intranet Scenario
– firewall + VPN and no NAT for VPN traffic
This is a common scenario where traffic to the public Internet goes through the Firewall/NAT only and traffic
between private networks is allowed without NAT before IPSec processing. The same authority administers
the networks that are protected by VPN to avoid any possible address clash. Configure each of the Internet
Security Router for the Intranet scenario using the following steps:
„ Configure VPN connection rules.
„ Configure Firewall access rules to allow inbound and outbound VPN traffic.
„ Configure a Firewall self rule to allow IKE packets into the Internet Security Router.

